Difference between revisions of "SSH server ldap user"
(Created page with "Category:Linux =SSH server - Authentication using LDAP server= Requirement: LDAP server ==Principle== The idea is to use a LDAP server to manage users and groups...") |
|||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Linux]] | [[Category:Linux]] | ||
| + | |||
| + | =Principle= | ||
| + | |||
| + | The idea is to use a LDAP server to manage users and groups to ease the maintenance and administration. | ||
| + | |||
| + | * Only 1 group of users is allowed to connect | ||
| + | |||
| + | * Access can be dynamically and easily granted | ||
| + | |||
| + | |||
| + | [[File:SSH_server_LDAP_user.png|none|SSH LDAP server authentication]] | ||
| + | |||
| + | |||
| + | |||
| + | =Server side requirements= | ||
| + | |||
| + | You need to have a '''[[LDAP server]]''' with both the '''"memberOf" and "Reference Integrity" overlays''' enabled. | ||
| + | |||
| + | |||
| + | |||
| + | You also need to create some '''group for SSH users''', this must be a ''groupOfNames'' - i.e not a ''posixGroup'' !!! | ||
| + | |||
| + | ==> Every member of the "ssh-users" group will be able to log-in to the server | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | =Client side requirements= | ||
| + | |||
| + | You must allow the SSH authentication by password | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | =LDAP client installation= | ||
| + | |||
| + | Install LDAP pam client | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | apt-get install libpam-ldap nscd ldap-utils | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | Questions / Answers | ||
| + | * LDAP URI? ldap://daxiongmao.eu || ldap://213.186.33.87 | ||
| + | * Distinguished Name: dc=daxiongmao,dc=eu | ||
| + | * LDAP version to use? 3 | ||
| + | * Make local root DB admin? Yes | ||
| + | * Does LDAP require login? No | ||
| + | * LDAP account for root: cn=admin,dc=daxiongmao,dc=eu | ||
| + | * LDAP root password: ROOT_PWD | ||
| + | |||
| + | |||
| + | [!] You can either use IP @ or name for LDAP server | ||
| + | |||
| + | |||
| + | [!] All these settings are available in /etc/ldap.conf | ||
| + | |||
| + | |||
| + | [!] If you make a mistake and need to change a value, you can go through the menu again by issuing this command: | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | dpkg-reconfigure ldap-auth-config | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | |||
| + | =Enable LDAP authentication= | ||
| + | |||
| + | |||
| + | ==LDAP as authentication server== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | vim /etc/ldap/ldap.conf | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | Adjust the file like that: | ||
| + | |||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | BASE dc=daxiongmao,dc=eu | ||
| + | URI ldap://daxiongmao.eu || ldap://213.186.33.87 | ||
| + | |||
| + | SIZELIMIT 0 | ||
| + | TIMELIMIT 0 | ||
| + | DEREF never | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | |||
| + | ==Allow LDAP lookups== | ||
| + | |||
| + | ''Automatic'' | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | auth-client-config -t nss -p lac_ldap | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | |||
| + | ''Manual approach'' | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | vim /etc/nsswitch.conf | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | * Replace "compat" by "files ldap" | ||
| + | |||
| + | * "files" allows sudo to check its local configuration before checking the LDAP-based | ||
| + | |||
| + | |||
| + | ==LDAP user's home== | ||
| + | |||
| + | This will create the LDAP user's home on server login. | ||
| + | |||
| + | |||
| + | Edit configuration file | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | vim /etc/pam.d/common-session | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | Add the following line BEFORE pam_ldap.so (~ line 28) | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | session required pam_mkhomedir.so skel=/etc/skel umask=0022 | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | |||
| + | =LDAP client configuration= | ||
| + | |||
| + | Edit LDAP's client configuration: | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | vim /etc/ldap.conf | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | ==Increase security== | ||
| + | |||
| + | Uncomment / comment | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | bind_policy soft ~ line 72 | ||
| + | |||
| + | #pam_password md5 ~ line 131 | ||
| + | pam_password crypt ~ line 138 | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | ==LDAP schema binding== | ||
| + | |||
| + | -- The following content depends on your configuration -- | ||
| + | |||
| + | |||
| + | Uncomment and adjust the following lines: | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | pam_filter objectclass=posixAccount ~ line 80 | ||
| + | pam_login_attribute uid ~ line 83 | ||
| + | |||
| + | |||
| + | nss_base_passwd ou=people,dc=daxiongmao,dc=eu?one ~ line 173 | ||
| + | nss_base_group ou=groups,dc=daxiongmao,dc=eu?sub?gidNumber=* ~ line 175 | ||
| + | nss_base_hosts ou=hosts,dc=daxiongmao,dc=eu ~ line 175 | ||
| + | nss_base_netgroup ou=groups,dc=daxiongmao,dc=eu ~ line 185 | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | [!] Note that the "passwd" (= user binding) must use the ''one'' scope ; the groups binding can use the ''sub'' scope. | ||
| + | |||
| + | |||
| + | ==allow LDAP Group ID== | ||
| + | |||
| + | This will allow use to LDAP Group ID = you don't have to create a local group with the same GID. | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | vim /etc/nsswitch.conf | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | Replace: "netgroup: nis" by | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | netgroup: nis ldap | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | Restart NSCD | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | /etc/init.d/nscd restart | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | |||
| + | ==Installation check== | ||
| + | |||
| + | |||
| + | ===Get all data=== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | ldapsearch -x | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | ===Get user list=== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | getent passwd | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | ===Get user settings=== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | getent passwd <user> | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | ===Get list of SSH users=== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | getent group ssh-users | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | |||
| + | ===Login as LDAP user=== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | su <user> | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | It should work smoothly ! :) | ||
| + | |||
| + | It might not even ask for a password !!! (Normal: you didn't restarted PAM so far) | ||
| + | |||
| + | |||
| + | |||
| + | =Overall config check= | ||
| + | |||
| + | You need to reboot your computer to enable all LDAP settings, including security ! | ||
| + | |||
| + | ==SSH test== | ||
| + | |||
| + | Test to SSH to the server using one LDAP account. | ||
| + | |||
| + | Since there is no filter (yet) all LDAP users should be able to log-in. | ||
| + | |||
| + | |||
| + | ==Local test== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | su <user> | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | >> It should ask for a password | ||
| + | |||
| − | |||
| − | |||
| + | =LDAP group filter= | ||
| − | |||
| − | + | Edit LDAP configuration | |
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | vim /etc/ldap.conf | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | '''Adjust the user binding''' (nss_base_passwd). | ||
| + | |||
| + | |||
| + | ==Single group binding== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | nss_base_passwd ou=people,dc=daxiongmao,dc=eu?one?memberof=cn=ssh-users,ou=groups,dc=daxiongmao,dc=eu | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | [!] you need a LDAP server with MemberOf enable !! | ||
| + | |||
| + | |||
| + | [!] mind the case ! overlay + {CN,OU,DC} in lower case !! | ||
| + | |||
| + | |||
| + | [!] you can only apply the scope "one" for it to work | ||
| + | |||
| + | |||
| + | ==Multi group binding== | ||
| + | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | nss_base_passwd ou=people,dc=daxiongmao,dc=eu?one?memberof=cn=ssh-users,ou=groups,dc=daxiongmao,dc=eu | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | ==Test== | ||
| + | |||
| + | All the changes in /etc/ldap.conf are read on real-time. | ||
| + | You should be able to test them right away ! | ||
| + | |||
| + | |||
| + | Only the "ssh-users" group's member should be able to log-in into the server now ! | ||
| + | |||
| − | |||
| − | |||
| − | |||
| + | =References= | ||
| + | * Digital Ocean - https://www.digitalocean.com/community/tutorials/how-to-authenticate-client-computers-using-ldap-on-an-ubuntu-12-04-vps | ||
| + | * Ubuntu official wiki - https://help.ubuntu.com/community/LDAPClientAuthentication | ||
| + | * Nice return of experience - http://kobi.nat.uni-magdeburg.de/patrick/pmwiki.php?n=Wiki.HOWTO-UbuntuLDAPAuthenticationLucidLynx | ||
| + | * Simple LDAP authentication - http://arthurdejong.org/nss-pam-ldapd/setup | ||
| + | * Nice information, especially for SUDO: https://www.secure-computing.net/wiki/index.php/OpenLDAP/Authentication | ||
| − | + | Related: | |
| + | * Digital Ocean "how to setup LDAP" - https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-a-basic-ldap-server-on-an-ubuntu-12-04-vps | ||
| − | + | User filters: http://linux.web.cern.ch/linux/docs/account-mgmt.shtml | |
Latest revision as of 15:29, 28 August 2014
Contents
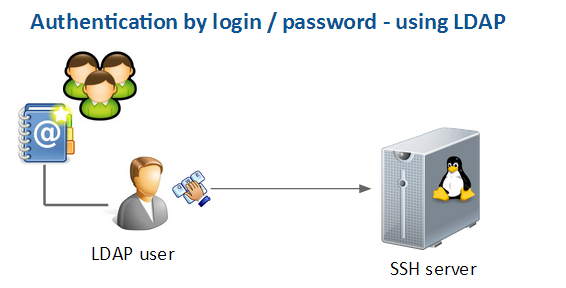
Principle
The idea is to use a LDAP server to manage users and groups to ease the maintenance and administration.
- Only 1 group of users is allowed to connect
- Access can be dynamically and easily granted
Server side requirements
You need to have a LDAP server with both the "memberOf" and "Reference Integrity" overlays enabled.
You also need to create some group for SSH users, this must be a groupOfNames - i.e not a posixGroup !!!
==> Every member of the "ssh-users" group will be able to log-in to the server
Client side requirements
You must allow the SSH authentication by password
LDAP client installation
Install LDAP pam client
apt-get install libpam-ldap nscd ldap-utils
Questions / Answers
- LDAP URI? ldap://daxiongmao.eu || ldap://213.186.33.87
- Distinguished Name: dc=daxiongmao,dc=eu
- LDAP version to use? 3
- Make local root DB admin? Yes
- Does LDAP require login? No
- LDAP account for root: cn=admin,dc=daxiongmao,dc=eu
- LDAP root password: ROOT_PWD
[!] You can either use IP @ or name for LDAP server
[!] All these settings are available in /etc/ldap.conf
[!] If you make a mistake and need to change a value, you can go through the menu again by issuing this command:
dpkg-reconfigure ldap-auth-config
Enable LDAP authentication
LDAP as authentication server
vim /etc/ldap/ldap.conf
Adjust the file like that:
BASE dc=daxiongmao,dc=eu
URI ldap://daxiongmao.eu || ldap://213.186.33.87
SIZELIMIT 0
TIMELIMIT 0
DEREF never
Allow LDAP lookups
Automatic
auth-client-config -t nss -p lac_ldap
Manual approach
vim /etc/nsswitch.conf
- Replace "compat" by "files ldap"
- "files" allows sudo to check its local configuration before checking the LDAP-based
LDAP user's home
This will create the LDAP user's home on server login.
Edit configuration file
vim /etc/pam.d/common-session
Add the following line BEFORE pam_ldap.so (~ line 28)
session required pam_mkhomedir.so skel=/etc/skel umask=0022
LDAP client configuration
Edit LDAP's client configuration:
vim /etc/ldap.conf
Increase security
Uncomment / comment
bind_policy soft ~ line 72
#pam_password md5 ~ line 131
pam_password crypt ~ line 138
LDAP schema binding
-- The following content depends on your configuration --
Uncomment and adjust the following lines:
pam_filter objectclass=posixAccount ~ line 80
pam_login_attribute uid ~ line 83
nss_base_passwd ou=people,dc=daxiongmao,dc=eu?one ~ line 173
nss_base_group ou=groups,dc=daxiongmao,dc=eu?sub?gidNumber=* ~ line 175
nss_base_hosts ou=hosts,dc=daxiongmao,dc=eu ~ line 175
nss_base_netgroup ou=groups,dc=daxiongmao,dc=eu ~ line 185
[!] Note that the "passwd" (= user binding) must use the one scope ; the groups binding can use the sub scope.
allow LDAP Group ID
This will allow use to LDAP Group ID = you don't have to create a local group with the same GID.
vim /etc/nsswitch.conf
Replace: "netgroup: nis" by
netgroup: nis ldap
Restart NSCD
/etc/init.d/nscd restart
Installation check
Get all data
ldapsearch -x
Get user list
getent passwd
Get user settings
getent passwd <user>
Get list of SSH users
getent group ssh-users
Login as LDAP user
su <user>It should work smoothly ! :)
It might not even ask for a password !!! (Normal: you didn't restarted PAM so far)
Overall config check
You need to reboot your computer to enable all LDAP settings, including security !
SSH test
Test to SSH to the server using one LDAP account.
Since there is no filter (yet) all LDAP users should be able to log-in.
Local test
su <user>>> It should ask for a password
LDAP group filter
Edit LDAP configuration
vim /etc/ldap.confAdjust the user binding (nss_base_passwd).
Single group binding
nss_base_passwd ou=people,dc=daxiongmao,dc=eu?one?memberof=cn=ssh-users,ou=groups,dc=daxiongmao,dc=eu[!] you need a LDAP server with MemberOf enable !!
[!] mind the case ! overlay + {CN,OU,DC} in lower case !!
[!] you can only apply the scope "one" for it to work
Multi group binding
nss_base_passwd ou=people,dc=daxiongmao,dc=eu?one?memberof=cn=ssh-users,ou=groups,dc=daxiongmao,dc=eu
Test
All the changes in /etc/ldap.conf are read on real-time. You should be able to test them right away !
Only the "ssh-users" group's member should be able to log-in into the server now !
References
- Digital Ocean - https://www.digitalocean.com/community/tutorials/how-to-authenticate-client-computers-using-ldap-on-an-ubuntu-12-04-vps
- Ubuntu official wiki - https://help.ubuntu.com/community/LDAPClientAuthentication
- Nice return of experience - http://kobi.nat.uni-magdeburg.de/patrick/pmwiki.php?n=Wiki.HOWTO-UbuntuLDAPAuthenticationLucidLynx
- Simple LDAP authentication - http://arthurdejong.org/nss-pam-ldapd/setup
- Nice information, especially for SUDO: https://www.secure-computing.net/wiki/index.php/OpenLDAP/Authentication
Related:
- Digital Ocean "how to setup LDAP" - https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-a-basic-ldap-server-on-an-ubuntu-12-04-vps
User filters: http://linux.web.cern.ch/linux/docs/account-mgmt.shtml