|
|
| (17 intermediate revisions by the same user not shown) |
| Line 1: |
Line 1: |
| − | =Installation=
| + | [[Category:Linux]] |
| | | | |
| − | By default Debian | Ubuntu doesn't include any SSH server.
| |
| − | <syntaxhighlight lang="bash">
| |
| − | apt-get install ssh openssh-server
| |
| − | </syntaxhighlight>
| |
| | | | |
| | + | =SSH client= |
| | | | |
| | | | |
| | + | ==Linux== |
| | | | |
| − | =SSH server configuration= | + | ===Standard login=== |
| − | | |
| − | | |
| − | Edit the configuration file:
| |
| | | | |
| | <syntaxhighlight lang="bash"> | | <syntaxhighlight lang="bash"> |
| − | vim /etc/ssh/sshd_config
| + | # syntax |
| − | </syntaxhighlight>
| + | ssh user@server -p portNumber |
| | | | |
| − | | + | # example |
| − | ==X11 forwarding==
| + | ssh root@daxiongmao.eu -p 4422 |
| − | | |
| − | In the configuration file, uncomment and set:
| |
| − | <syntaxhighlight lang="bash">
| |
| − | ForwardAgent yes
| |
| − | ForwardX11 yes
| |
| − | ForwardX11Trusted yes
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | '''Enable | Disable the forwarding:'''
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | # This server doesn’t have a XServer. Therefore do not forward graphical data.
| |
| − | X11Forwarding no
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ==Port(s) number==
| |
| − | | |
| − | You can listen on multiple port. Just do the following:
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | Port 22
| |
| − | Port 2200
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | Security psycho mode:
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | # The default port SSH is 22. You may want to change that port to another one so your server will be more discreet.
| |
| − | # NB: if your server is hosted the provider might need access for maintenance purposes. | |
| − | Port XXXXX
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | | |
| − | ==Restart SSH server==
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | /etc/init.d/ssh restart
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | =SSH server configuration - Authentication by Linux user login / password=
| |
| − | | |
| − | ==Principle==
| |
| − | | |
| − | This is the default authentication system.
| |
| − | | |
| − | | |
| − | Each user that has a '''local account on the server''' and member is allowed to access the SSH server with its login / password.
| |
| − | | |
| − | [[File:SSH server default auth.png|none|SSH default authentication system]]
| |
| − | | |
| − | | |
| − | | |
| − | ==Configuration changes==
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | vim /etc/ssh/sshd_config
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ===Protocol and password enforcement===
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | Protocol 2 # only use SSH v2
| |
| − | PermitRootLogin no # Avoid root connections
| |
| − | PermitEmptyPassword no # Forbidden user with empty passwords
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ===Login time===
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | # Time to log
| |
| − | LoginGraceTime 30
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ==Restart SSH server==
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | /etc/init.d/ssh restart
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | | |
| − | =SSH server configuration - Authentication with RSA keys=
| |
| − | | |
| − | | |
| − | ==Introduction==
| |
| − | | |
| − | If you’d like to increase the authentication process you can use authentication by private/public key.
| |
| − | * Generate new private / public keys on your own computer
| |
| − | * Put the public key on the remote SSH server
| |
| − | * Only the person with the private key can be authenticate on the server
| |
| − | | |
| − | | |
| − | [[File:SSH_server_RSA_keys.png|none|SSH RSA authentication]]
| |
| − | | |
| − | | |
| − | | |
| − | For instance, this is how hosting company such as OVH can log on your system.
| |
| − | | |
| − | | |
| − | | |
| − | '''Security improvement: remove password authentication'''
| |
| − | | |
| − | When the key authentication is working you can remove the default access by login / password.
| |
| − | Then, only people with a valid private/public key pair can log in.
| |
| − | | |
| − | That way, there is no way for brute-force attacks to be successful, so your system is more secure.
| |
| − | | |
| − | | |
| − | | |
| − | ==Declare the public key on the server==
| |
| − | | |
| − | | |
| − | You have to:
| |
| − | * '''log in''' to your SSH server with the '''user that’s gonna use this key'''
| |
| − | * Go to '''user's home''' directory
| |
| − | * Create a '''.ssh''' folder (if there was none before).
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | cd ~
| |
| − | mkdir .ssh
| |
| − | cd .ssh
| |
| | </syntaxhighlight> | | </syntaxhighlight> |
| | | | |
| | | | |
| − | Add the new ''public'' key to the list of allowed keys:
| + | ===Using RSA key=== |
| | | | |
| − | <syntaxhighlight lang="bash">
| + | Key points: |
| − | vim authorized_key2
| + | * The key must belongs to the current user |
| − | </syntaxhighlight>
| + | * The key rights must be "500" |
| | | | |
| | | | |
| − | Prefix your key with:
| + | Then you can log-in using the following command: |
| − | * RSA: ssh-rsa
| |
| − | * DSA: ssh-dss
| |
| − | | |
| − | Then paste the public key in one line - the public key mustn't be change or separated in 2 lines!
| |
| − | | |
| | | | |
| | <syntaxhighlight lang="bash"> | | <syntaxhighlight lang="bash"> |
| − | # Example:
| + | ssh -i Guillaume_OpenSSH.private -p 2200 guillaume@dev.daxiongmao.eu |
| − | ssh-rsa AAAAB3NzaC1yc2EA[...]Lg5whU0zMuYE5IZu8ZudnP6ds= myname@example.com | |
| − | ssh-dss AAAAB3NzaC1yc2EA[...]Lg5whU0zMuYE5IZu8ZudnP6ds= myname@example.com
| |
| | </syntaxhighlight> | | </syntaxhighlight> |
| | | | |
| | + | Where: |
| | + | * '''-i''' ''myFile'' = the private key you have to use |
| | + | * '''-p''' ''port'' = specific port number (if not default 22) |
| | | | |
| − | Adjust file rights, the ''authorized_keys2'' file must be write/readable only by that user
| |
| − |
| |
| − | <syntaxhighlight lang="bash">
| |
| − | chmod 600 authorized_keys2
| |
| − | cd ..
| |
| − | chmod 700 .ssh
| |
| − | </syntaxhighlight>
| |
| − |
| |
| − |
| |
| − |
| |
| − | ==How-to generate private / public keys in Windows==
| |
| − |
| |
| − | You can generate private / public keys with '''PuttyGen''' = Putty key generator.
| |
| | | | |
| | | | |
| − | [[File:SSH_putty_key_generator.png|none|puttyGen first step]]
| + | ===X11 forwarding=== |
| − | | |
| − | | |
| − | When the keys are OK, you have to enter a key pass-phrase. Your pass-phrase must be:
| |
| − | * long (> 15 characters)
| |
| − | * hard to guess
| |
| − | * with letters + signs + numbers
| |
| − | | |
| − | | |
| − | '''Reminder'''
| |
| − | | |
| − | how to choose your passphrase and protect it: http://www.alcf.anl.gov/resource-guides/user-authentication-policies
| |
| − | | |
| − | | |
| − | [[File:SSH_putty_key_generator_2.png|none|PuttyGen 2nd step]]
| |
| − | | |
| − | | |
| − | Then, save your keys!
| |
| − | You should be the only one to access the save location.
| |
| − | | |
| − | | |
| − | | |
| − | ==Configuration changes== | |
| | | | |
| | <syntaxhighlight lang="bash"> | | <syntaxhighlight lang="bash"> |
| − | vim /etc/ssh/sshd_config
| + | ssh -X guillaume@nuc-media-center |
| | </syntaxhighlight> | | </syntaxhighlight> |
| | | | |
| | | | |
| − | ===Allow empty password===
| + | ♦ Note that the remote computer have X11 installed and X11 applications. |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | PermitEmptyPassword yes # allow empty password in favor of RSA keys
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | | |
| − | ==Restart SSH server==
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | /etc/init.d/ssh restart
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | Create profile
| |
| − |
| |
| − | Auto-login
| |
| − |
| |
| − | | |
| − | | |
| − | | |
| − | Attach private key
| |
| − |
| |
| − | | |
| − | Save profile
| |
| − | Go back to the main screen Session and save your changes.
| |
| − |
| |
| − | | |
| − | Click on “open” to initialize connection.
| |
| − | | |
| − | Login procedure
| |
| − | | |
| − | Type your passphrase on system request
| |
| − |
| |
| − | | |
| − | Access is granted!
| |
| − | | |
| − | Disable standard username / password login
| |
| − | | |
| − | Edit the configuration file
| |
| − | # vim /etc/ssh/sshd_config
| |
| − | | |
| − | Adjust the line:
| |
| − |
| |
| − | | |
| − | to:
| |
| − |
| |
| − | | |
| | | | |
| | | | |
| − | =Fail2ban=
| |
| | | | |
| − | see [[Fail2ban#SSH_configuration]]
| + | ==Windows== |
| | | | |
| | + | You have to use Putty to perform SSH login. |
| | | | |
| | | | |
| | + | '''How to add a public / private key in Putty ?''' |
| | | | |
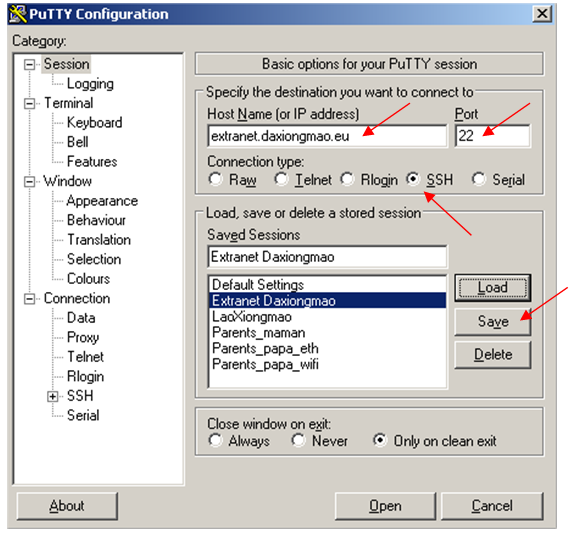
| | + | 1.Create profile |
| | | | |
| | + | [[File:Putty_SSH_access_1.png|none|Putty SSH login step 1]] |
| | | | |
| | | | |
| − | =SSH client=
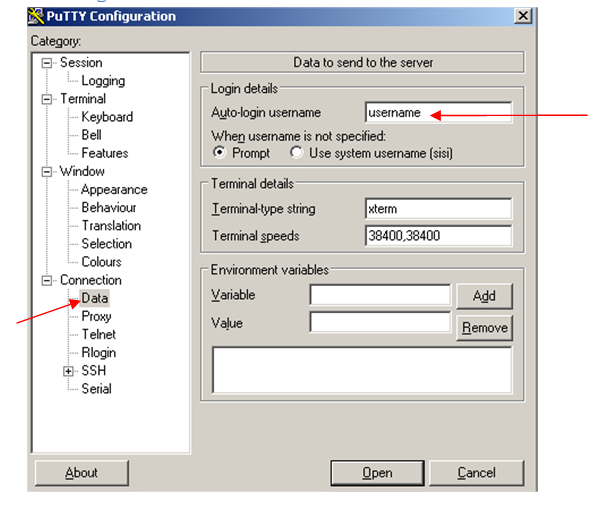
| + | 2. Auto-login |
| − | | |
| − | | |
| − | ==Linux==
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | # syntax
| |
| − | ssh user@server -p portNumber
| |
| − | | |
| − | # example
| |
| − | ssh root@daxiongmao.eu -p 4422
| |
| − | </syntaxhighlight>
| |
| − | | |
| | | | |
| | + | [[File:Putty_SSH_access_2.png|none|Putty SSH login step 2]] |
| | | | |
| | | | |
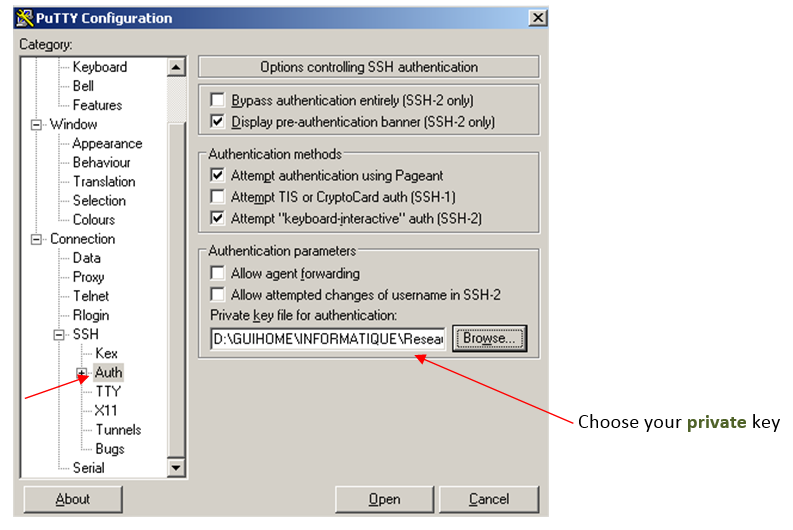
| | + | 3. Attach private key |
| | | | |
| − | =References=
| + | [[File:Putty_SSH_access_3.png|none|Putty SSH login step 3]] |
| | | | |
| | | | |
| − | Source: http://www.howtoforge.com/ssh_key_based_logins_putty
| + | 4. Save profile |
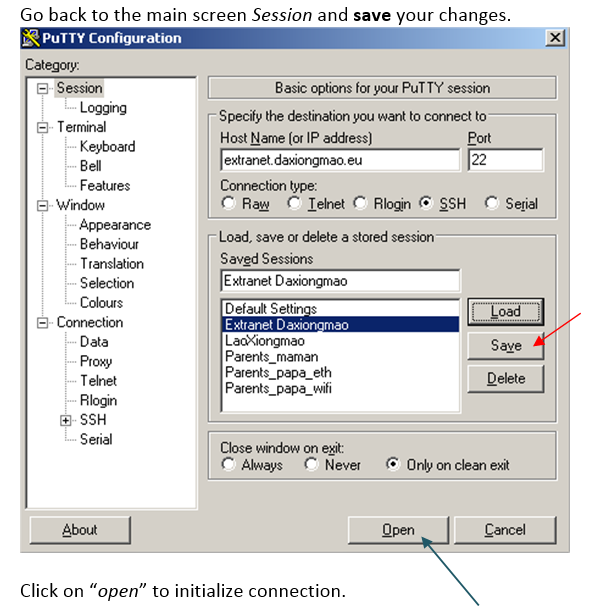
| | | | |
| − | Windows - putty software: http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
| + | [[File:Putty_SSH_access_4.png|none|Putty SSH login step 4]] |