|
|
| (49 intermediate revisions by the same user not shown) |
| Line 1: |
Line 1: |
| | + | [[Category:Linux]] |
| | The firewall (FW) is a key component of your server's security. | | The firewall (FW) is a key component of your server's security. |
| | | | |
| | + | You can search Internet to get all the related theory. My aim is not to explain that over here but just to give you HOW to setup a Firewall with IpTables. |
| | | | |
| | + | The following codes and examples are based '''iptables''' and '''ip6tables'''. |
| | | | |
| − | =Key points=
| |
| | | | |
| | | | |
| − | ==Default policy== | + | =Principle= |
| | | | |
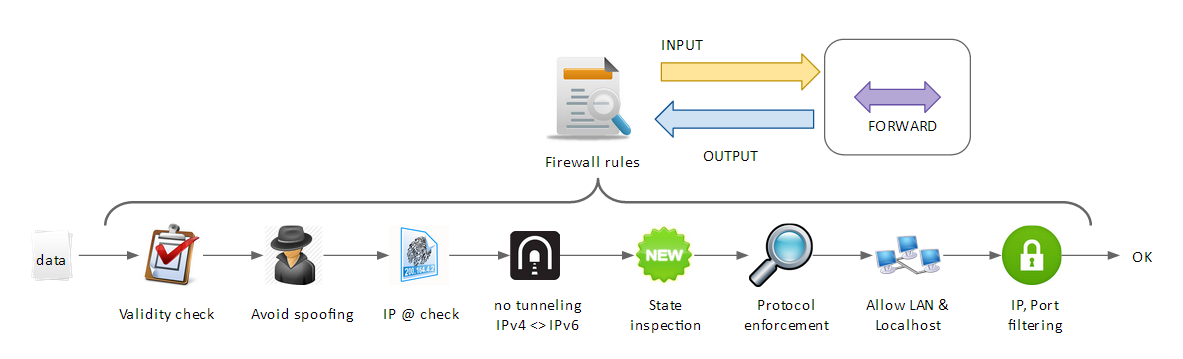
| − | This is how you defined a default policy. | + | This is how a firewall works: |
| | | | |
| | + | [[File:FW_principle.png|none|FW principle]] |
| | | | |
| − | Note:
| |
| − | * You have to adjust the policy to your own settings
| |
| − | * You should NOT set the INPUT in ACCEPT mode. That's risky!
| |
| | | | |
| | | | |
| − | <syntaxhighlight lang="bash">
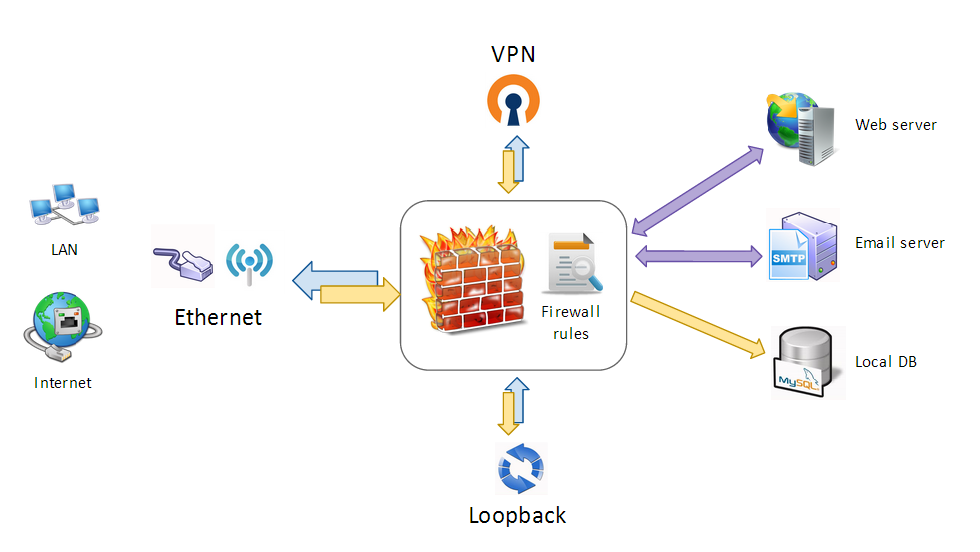
| + | This is how you can use a firewall at home | work: |
| − | IPTABLES=`which iptables`
| |
| | | | |
| − | echo -e " "
| + | [[File:FW_usage.png|none|FW usage]] |
| − | echo -e "------------------------"
| |
| − | echo -e " Flush existing rules "
| |
| − | echo -e "------------------------"
| |
| | | | |
| − | $IPTABLES -t filter -F
| |
| − | $IPTABLES -t filter -X
| |
| | | | |
| − | # delete NAT rules
| |
| − | $IPTABLES -t nat -F
| |
| − | $IPTABLES -t nat -X
| |
| | | | |
| − | # delete MANGLE rules (packets modifications)
| + | The firewall performs: |
| − | $IPTABLES -t mangle -F
| + | * Basic security check |
| − | $IPTABLES -t mangle -X
| + | * Security policy's enforcement |
| | + | * IP, port filtering |
| | + | * Port forwarding and NAT |
| | | | |
| − | echo -e " "
| |
| − | echo -e "------------------------"
| |
| − | echo -e " Default policy"
| |
| − | echo -e "------------------------"
| |
| − | echo -e " || --> OUTGOING reject all "
| |
| − | echo -e " --> || INCOMING reject all "
| |
| − | echo -e " --> || --> FORWARDING accept all (each redirection needs configuration)"
| |
| | | | |
| − | # INCOMING = avoid intrusions
| |
| − | # OUTGOING = avoid disclosure of sensitive / private data
| |
| − | $IPTABLES -P INPUT DROP
| |
| − | $IPTABLES -P FORWARD ACCEPT
| |
| − | $IPTABLES -P OUTPUT ACCEPT
| |
| | | | |
| − | echo -e " ... Reject invalid packets"
| + | =Next steps= |
| − | $IPTABLES -A INPUT -p tcp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A INPUT -p udp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A INPUT -p icmp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A OUTPUT -p tcp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A OUTPUT -p udp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A OUTPUT -p icmp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A FORWARD -p tcp -m state --state INVALID -j DROP
| |
| − | $IPTABLES -A FORWARD -p udp -m state --state INVALID -j DROP
| |
| | | | |
| − | echo -e " ... Keep ESTABLISHED connections "
| + | See [[Template:Menu_content_security#Firewall]] |
| − | $IPTABLES -A INPUT -m state --state ESTABLISHED -j ACCEPT
| |
| − | $IPTABLES -A FORWARD -m state --state ESTABLISHED -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -m state --state ESTABLISHED -j ACCEPT
| |
| | | | |
| − | echo -e " ... Keep RELATED connections (required for FTP)"
| + | =Note= |
| − | $IPTABLES -A INPUT -m state --state RELATED -j ACCEPT
| |
| − | $IPTABLES -A FORWARD -m state --state RELATED -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -m state --state RELATED -j ACCEPT
| |
| | | | |
| − | # Allow localhost communication
| + | All this knowledge is the result of years of experiments and trials. Don't hesitate to search over Internet for more advanced || simpler rules. |
| − | echo -e " ... Allow localhost"
| |
| − | $IPTABLES -A INPUT -i lo -s 127.0.0.0/24 -d 127.0.0.0/24 -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -o lo -s 127.0.0.0/24 -d 127.0.0.0/24 -j ACCEPT
| |
| | | | |
| − | </syntaxhighlight>
| |
| | | | |
| | | | |
| − | ==DHCP==
| |
| | | | |
| − | You need to following to use DHCP:
| + | =References= |
| | | | |
| − | <syntaxhighlight lang="bash">
| + | * My education at Telecom Bretagne [http://www.telecom-bretagne.eu/] && Chalmers [http://www.chalmers.se/en/] |
| − | IPTABLES=`which iptables`
| |
| | | | |
| − | # DHCP client >> Broadcast IP request
| + | * How to set IPv4 as default: http://bruteforce.gr/make-apt-get-use-ipv4-instead-ipv6.html |
| − | $IPTABLES -A OUTPUT -p udp -d 255.255.255.255 --sport 68 --dport 67 -j ACCEPT
| |
| − | # DHCP server >> send / reply to IPs requests
| |
| − | $IPTABLES -A INPUT -p udp -s 255.255.255.255 --sport 67 --dport 68 -j ACCEPT
| |
| − | </syntaxhighlight>
| |
| | | | |
| − | | + | * Working years and some co-workers help: |
| − | ==DNS==
| + | ** Julien Rialland |
| − | | |
| − | This will allow your computer to perform DNS requests:
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | IPTABLES=`which iptables`
| |
| − | | |
| − | $IPTABLES -A OUTPUT -p udp --dport 53 -m limit --limit 100/s -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p udp --sport 53 -m limit --limit 100/s -j ACCEPT
| |
| − | $IPTABLES -A INPUT -p udp --sport 53 -m limit --limit 100/s -j ACCEPT
| |
| − | $IPTABLES -A INPUT -p udp --dport 53 -m limit --limit 100/s -j ACCEPT
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ==LAN communication==
| |
| − | | |
| − | To allow communication in the local network, without any restrictions:
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | IPTABLES=`which iptables`
| |
| − | LAN_ADDRESS="172.16.50.0/24"
| |
| − | | |
| − | $IPTABLES -A INPUT -s $LAN_ADDRESS -d $LAN_ADDRESS -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -s $LAN_ADDRESS -d $LAN_ADDRESS -j ACCEPT
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ==FTP client==
| |
| − | | |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | IPTABLES=`which iptables`
| |
| − | | |
| − | # FTP client - base rules
| |
| − | $IPTABLES -A INPUT -p tcp --sport 21 -m state --state ESTABLISHED -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p tcp --dport 21 -m state --state NEW,ESTABLISHED -j ACCEPT
| |
| − | | |
| − | # Active FTP
| |
| − | $IPTABLES -A INPUT -p tcp --sport 20 -m state --state ESTABLISHED,RELATED -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p tcp --dport 20 -m state --state ESTABLISHED -j ACCEPT
| |
| − | | |
| − | # Passive FTP
| |
| − | $IPTABLES -A INPUT -p tcp --sport 1024: --dport 1024: -m state --state ESTABLISHED -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p tcp --sport 1024: --dport 1024: -m state --state ESTABLISHED,RELATED -j ACCEPT
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | ==VPN==
| |
| − | | |
| − | Adjust the following to your own port, network ID and protocol:
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | IPTABLES=`which iptables`
| |
| − | | |
| − | INT_ETH=eth0
| |
| − | IP_LAN_ETH=`/sbin/ifconfig $INT_ETH | grep 'inet addr:' | cut -d: -f2 | awk '{ print $1}'`
| |
| − | | |
| − | INT_VPN=tun0
| |
| − | VPN_PORT="8080"
| |
| − | VPN_PROTOCOL="udp"
| |
| − | LAN_ADDRESS_VPN="172.16.60.0/24"
| |
| − | | |
| − | echo -e " "
| |
| − | echo -e "------------------------"
| |
| − | echo -e " VPN configuration"
| |
| − | echo -e "------------------------"
| |
| − | | |
| − | echo " "
| |
| − | echo -e "# VPN interface : $INT_VPN"
| |
| − | echo -e "# VPN IP @ : $LAN_ADDRESS_VPN"
| |
| − | echo -e "# VPN port : $VPN_PORT"
| |
| − | echo -e "# VPN protocol : $VPN_PROTOCOL"
| |
| − | echo -e "-------------------------------------- "
| |
| − | | |
| − | # Allow devices communication $ETH0 <--> tun0
| |
| − | $IPTABLES -t nat -A POSTROUTING -s $LAN_ADDRESS_VPN -o $INT_ETH -j MASQUERADE
| |
| − | $IPTABLES -A FORWARD -s $LAN_ADDRESS_VPN -j ACCEPT
| |
| − | | |
| − | echo -e " ... Allow VPN connections"
| |
| − | $IPTABLES -A INPUT -p $VPN_PROTOCOL --dport $VPN_PORT -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p tcp --dport $VPN_PORT -j ACCEPT
| |
| − | | |
| − | echo -e " ... Allow everything to go through VPN - all INPUT,OUTPUT,FORWARD"
| |
| − | $IPTABLES -A INPUT -i $INT_VPN -m state ! --state INVALID -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -o $INT_VPN -m state ! --state INVALID -j ACCEPT
| |
| − | $IPTABLES -A FORWARD -o $INT_VPN -m state ! --state INVALID -j ACCEPT
| |
| − | | |
| − | echo -e " ... Allow VPN network communication (required for client <> client comm.)"
| |
| − | $IPTABLES -A INPUT -s $LAN_ADDRESS_VPN -d $LAN_ADDRESS_VPN -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -s $LAN_ADDRESS_VPN -d $LAN_ADDRESS_VPN -j ACCEPT
| |
| − | </syntaxhighlight>
| |
| − | | |
| − | | |
| − | | |
| − | | |
| − | =Servers=
| |
| − | | |
| − | | |
| − | ==DHCP==
| |
| − | | |
| − | | |
| − | This is how you enable a DHCP server with TFTP (netBoot) :
| |
| − | | |
| − | <syntaxhighlight lang="bash">
| |
| − | IPTABLES=`which iptables`
| |
| − | | |
| − | # Allow LAN communication
| |
| − | # ... Required for NFS and the NetBoot ...
| |
| − | $IPTABLES -A INPUT -s $LAN_ADDRESS -d $LAN_ADDRESS -m state ! --state INVALID -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -s $LAN_ADDRESS -d $LAN_ADDRESS -m state ! --state INVALID -j ACCEPT
| |
| − |
| |
| − | ########################
| |
| − | # INPUT filters
| |
| − | ########################
| |
| − |
| |
| − | ##### DHCP client ######
| |
| − | # Broadcast IP request
| |
| − | $IPTABLES -A OUTPUT -p udp -d 255.255.255.255 --sport 68 --dport 67 -j ACCEPT
| |
| − | # Send / reply to IPs requests
| |
| − | $IPTABLES -A INPUT -p udp -s 255.255.255.255 --sport 67 --dport 68 -j ACCEPT
| |
| − |
| |
| − | ###### DHCP server ######
| |
| − | # Received client's requests
| |
| − | $IPTABLES -A INPUT -p udp --sport 68 --dport 67 -j ACCEPT
| |
| − | $IPTABLES -A INPUT -p tcp --sport 68 --dport 67 -j ACCEPT
| |
| − | | |
| − | # NetBoot - TFTP server
| |
| − | $IPTABLES -A INPUT -p udp -s $LAN_ADDRESS --dport 69 -j ACCEPT
| |
| − |
| |
| − |
| |
| − | ########################
| |
| − | # OUTPUT filters
| |
| − | ########################
| |
| − | # DHCP [udp]
| |
| − | $IPTABLES -A OUTPUT -p udp --dport 67 -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p udp --dport 68 -j ACCEPT
| |
| − | # DHCP [tcp]
| |
| − | $IPTABLES -A OUTPUT -p tcp --dport 67 -j ACCEPT
| |
| − | $IPTABLES -A OUTPUT -p tcp --dport 68 -j ACCEPT
| |
| − |
| |
| − | # TFTP NetBoot
| |
| − | $IPTABLES -A OUTPUT -p udp --dport 69 -j ACCEPT
| |
| − | </syntaxhighlight>
| |