Firewall FORWARD filters
Contents
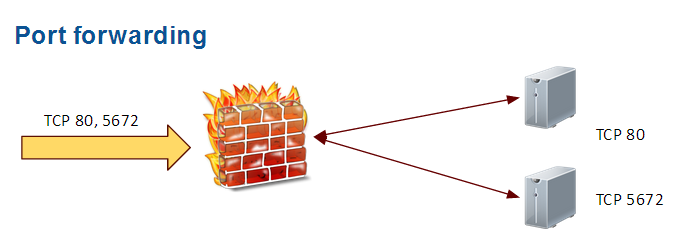
Port forwarding principle
The aim is to reach a server located behind the actual server we are working on.
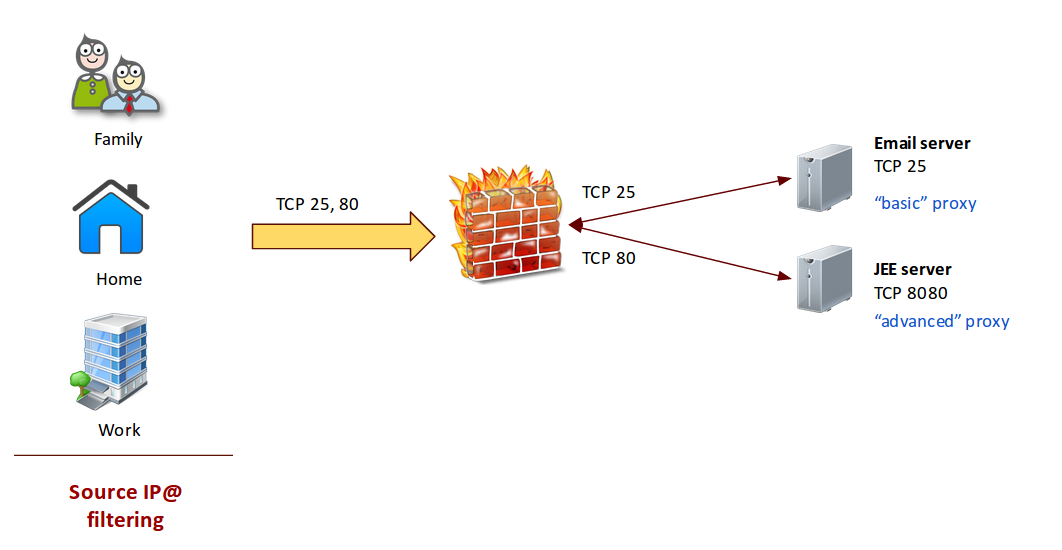
Basic proxy
In this case the target port number is the same as the source port.
This is a RISK because we exposed to Internet the schema of our Network.
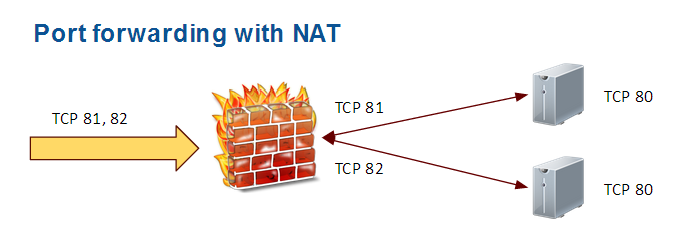
Advanced proxy
Here, the source and target port numbers are different. That's better but you need to maintain a 'IN / OUT ports matching table' as IT admin.
How to
To do a port forwarding you have to:
- Allow some source IP / hosts to use forwarding
- Create some forward target
- Open the incoming port [input + output]
- Register the target server and allow POST-ROUTING operations on it
- Route the incoming port to the target server + port number
Requirements:
- Enable port forwading
- The current server must be able to reach the target {server,port}
IpTables script
You have to declare the following only ONCE in all your FW script:
Enable module
#### Requirement: enable port forwarding in general
echo 1 > /proc/sys/net/ipv4/conf/eth0/forwarding
echo 1 > /proc/sys/net/ipv6/conf/all/forwarding
### Allow forward from IP@...
$IPTABLES -A FORWARD -s 91.121.17.114 -j ACCEPT # work
$IPTABLES -A FORWARD -s 5.39.81.23 -j ACCEPT # family VPN
$IPTABLES -A FORWARD -s 192.168.18.0 -j ACCEPT # home
### Open incoming ports [=from ports]...
$IPTABLES -A INPUT -p tcp --dport 25 -j ACCEPT
$IPTABLES -A INPUT -p tcp --dport 80 -j ACCEPT
### Open target ports [=to ports]...
$IPTABLES -A OUTPUT -p tcp --dport 25 -j ACCEPT
$IPTABLES -A OUTPUT -p tcp --dport 8080 -j ACCEPT
### Declare forward targets [=to]...
$IPTABLES -A POSTROUTING -d 192.168.18.2 -t nat -j MASQUERADE # Email server
$IPTABLES -A POSTROUTING -d 192.168.18.5 -t nat -j MASQUERADE # JEE server
### Redirect FROM (IP:port) TO (server:port)
$IPTABLES -A PREROUTING -t nat -p tcp --dport 25 -j DNAT --to 192.168.18.2:25
$IPTABLES -A PREROUTING -t nat -p tcp --dport 80 -j DNAT --to 192.168.18.5:8080
IpTables function
function allowForwardingFromTo {
### Allow forwarding from/to specific source IP@ and networks
# Remote IP @
$IPTABLES -A FORWARD -s 5.39.81.23 -j ACCEPT
$IPTABLES -A FORWARD -s 193.12.118.194 -j ACCEPT
$IPTABLES -A FORWARD -s 193.12.118.195 -j ACCEPT
$IPTABLES -A FORWARD -s 193.12.118.196 -j ACCEPT
# LAN
if [ ! -z "$IP_LAN_V4" ] ; then
$IPTABLES -A FORWARD -s $IP_LAN_V4 -j ACCEPT
fi
# VPN
if [ ! -z "$IP_LAN_VPN_PRV" ] ; then
$IPTABLES -A FORWARD -s $IP_LAN_VPN_PRV -j ACCEPT
fi
}
function forwardPort {
SOURCE_PORT=$1
PROTOCOL=$2
TARGET_SERVER=$3
TARGET_PORT=$4
$IPTABLES -A INPUT -p $PROTOCOL --dport $SOURCE_PORT -j ACCEPT
$IPTABLES -A OUTPUT -p $PROTOCOL --dport $TARGET_PORT -j ACCEPT
$IPTABLES -A PREROUTING -t nat -p $PROTOCOL --dport $SOURCE_PORT -j DNAT --to $TARGET_SERVER:$TARGET_PORT
}
#######################
# usage example
######################
allowForwardingFromTo
forwardPort 80 tcp 192.168.12.3 8080
forwardPort 51000 tcp 192.168.12.3 9000
Port forwarding VS proxy
Usually it's better to proxy than forward.
So if you can use the Apache2 proxy to redirect "http://mysite/myApp" to your sub-server Apache2 "/myApp" - DO IT !
My advice:
Only use port forwarding when there are no other choice.