Difference between revisions of "Email relay"
| Line 136: | Line 136: | ||
| − | =Test | + | =Test your configuration= |
<syntaxhighlight lang="bash"> | <syntaxhighlight lang="bash"> | ||
Revision as of 12:07, 21 January 2017
Contents
Principle
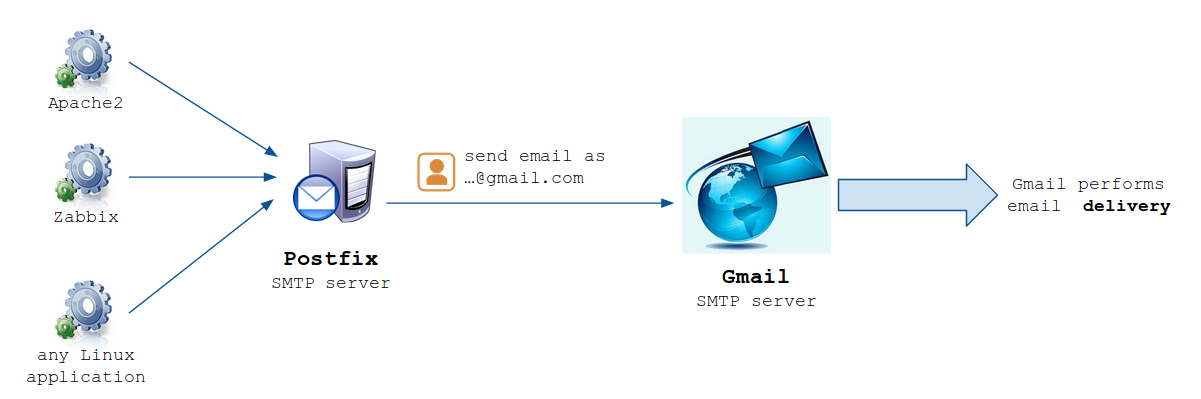
Our server will forward all emails to another SMTP server. The SMTP server we're gonna install is stupid: only local domain, no account checking, no anti-virus or spam protection.
- From a local point of view, all emails are send using Linux default configuration and system users
- From the other hand - the big SMTP server ("Gmail", "Outlook", ...) - all emails come from the same account
Principle:
As you can see, POSTFIX SMTP server will just act as a proxy between local services and Gmail.
When to use it ?
If you only have a single server and want to monitor it, then use a relay! That's much easier than setup a complete email server. It's also easier to maintain!
Installation
apt-get install postfix mailutils libsasl2-2 ca-certificates libsasl2-modulesChoose:
- Internet Site
- Type your FQDN like: dev.daxiongmao.eu || smartcard-gw.smartcards.vehco.com
Configuration
POSTFIX global conf
Edit Postfix configuration
vim /etc/postfix/main.cf
Add / adjust the SMTP relay and SASL settings (~ line 37)
## SMTP relay
relayhost = [smtp.gmail.com]:587
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_password
smtp_sasl_security_options = noanonymous
smtp_sasl_tls_security_options = noanonymous
smtp_tls_policy_maps = hash:/etc/postfix/tls_policy
Do not change the default TLS settings !!
Credentials file
Create login / password file
vim /etc/postfix/sasl_password
Put the following content
[smtp.gmail.com]:587 USERNAME@gmail.com:PASSWORD
Set rights
chmod 640 /etc/postfix/sasl_password
chown postfix:postfix /etc/postfix/sasl_password
Compute new hash for postfix
chown -R postfix /etc/postfix
postmap /etc/postfix/sasl_password
TLS policy
Create TLS policy file
vim /etc/postfix/tls_policy
Put the following content
[smtp.gmail.com]:587 encrypt
Compute new hash for postfix
postmap /etc/postfix/tls_policy
Apply changes
You must restart POSTFIX to apply changes
service postfix restart
Test your configuration
echo "Test from my new SMTP relay" | mail -s "Test Postfix SMTP relay" target@domain.com
## Multi-users
echo "Test from my new SMTP relay" | mail -s "Test Postfix SMTP relay" target@domain.com,target2@domain.com
Check your logs!! ... see below
Logs
Application logs
cat /var/log/mail.log
You should see something like:
Aug 13 10:15:46 smartcard-gw postfix/pickup[11711]: 558D442DDF: uid=0 from=<root@dev>
Aug 13 10:15:46 smartcard-gw postfix/cleanup[11836]: 558D442DDF: message-id=<20140813081546.558D442DDF@dev>
Aug 13 10:15:46 smartcard-gw postfix/qmgr[11712]: 558D442DDF: from=<root@dev.daxiongmao.eu>, size=361, nrcpt=1 (queue active)
Aug 13 10:15:48 smartcard-gw postfix/smtp[11838]: 558D442DDF: to=<target@domain.com>, relay=smtp.gmail.com[173.194.71.108]:587, delay=2.4, delays=0.02/0.04/0.89/1.5, dsn=2.0.0, status=sent (250 2.0.0 OK 1407917748 n2sm761208lag.18 - gsmtp)
Aug 13 10:15:48 smartcard-gw postfix/qmgr[11712]: 558D442DDF: removed
Error Log
cat /var/log/mail.errit should be empty
Usage
The usage is transparent.
A lot of services like Zabbix, Nagios, Webmin... are already using the "mail" application. So you don't need to do anything on your side! :-)