Difference between revisions of "SSH Client"
| Line 211: | Line 211: | ||
Then, save your keys! | Then, save your keys! | ||
You should be the only one to access the save location. | You should be the only one to access the save location. | ||
| − | |||
| − | |||
| Line 223: | Line 221: | ||
| − | === | + | ===Allow empty password=== |
| − | |||
| − | |||
| + | <syntaxhighlight lang="bash"> | ||
| + | PermitEmptyPassword yes # allow empty password in favor of RSA keys | ||
| + | </syntaxhighlight> | ||
| Line 237: | Line 236: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Create profile | Create profile | ||
| Line 326: | Line 271: | ||
to: | to: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Revision as of 14:47, 6 June 2014
Contents
Installation
By default Debian | Ubuntu doesn't include any SSH server.
apt-get install ssh openssh-server
SSH server configuration
Edit the configuration file:
vim /etc/ssh/sshd_config
X11 forwarding
In the configuration file, uncomment and set:
ForwardAgent yes
ForwardX11 yes
ForwardX11Trusted yes
Enable | Disable the forwarding:
# This server doesn’t have a XServer. Therefore do not forward graphical data.
X11Forwarding no
Port(s) number
You can listen on multiple port. Just do the following:
Port 22
Port 2200
Security psycho mode:
# The default port SSH is 22. You may want to change that port to another one so your server will be more discreet.
# NB: if your server is hosted the provider might need access for maintenance purposes.
Port XXXXX
Restart SSH server
/etc/init.d/ssh restart
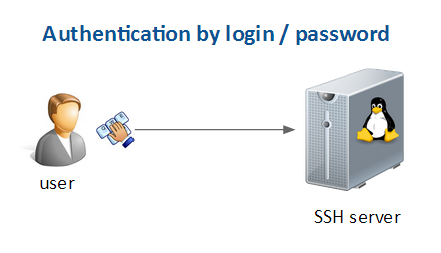
SSH server configuration - Authentication by Linux user login / password
Principle
This is the default authentication system.
Each user that has a local account on the server and member is allowed to access the SSH server with its login / password.
Configuration changes
vim /etc/ssh/sshd_config
Protocol and password enforcement
Protocol 2 # only use SSH v2
PermitRootLogin no # Avoid root connections
PermitEmptyPassword no # Forbidden user with empty passwords
Login time
# Time to log
LoginGraceTime 30
Restart SSH server
/etc/init.d/ssh restart
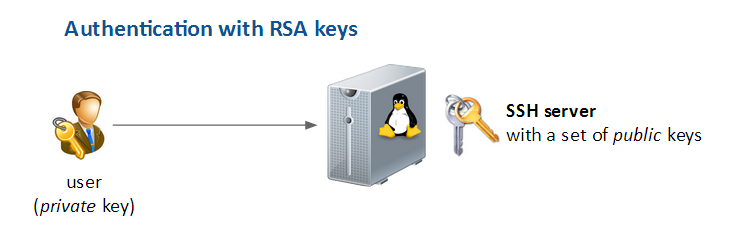
SSH server configuration - Authentication with RSA keys
Introduction
If you’d like to increase the authentication process you can use authentication by private/public key.
- Generate new private / public keys on your own computer
- Put the public key on the remote SSH server
- Only the person with the private key can be authenticate on the server
For instance, this is how hosting company such as OVH can log on your system.
Security improvement: remove password authentication
When the key authentication is working you can remove the default access by login / password. Then, only people with a valid private/public key pair can log in.
That way, there is no way for brute-force attacks to be successful, so your system is more secure.
Declare the public key on the server
You have to:
- log in to your SSH server with the user that’s gonna use this key
- Go to user's home directory
- Create a .ssh folder (if there was none before).
cd ~
mkdir .ssh
cd .ssh
Add the new public key to the list of allowed keys:
vim authorized_key2
Prefix your key with:
- RSA: ssh-rsa
- DSA: ssh-dss
Then paste the public key in one line - the public key mustn't be change or separated in 2 lines!
# Example:
ssh-rsa AAAAB3NzaC1yc2EA[...]Lg5whU0zMuYE5IZu8ZudnP6ds= myname@example.com
ssh-dss AAAAB3NzaC1yc2EA[...]Lg5whU0zMuYE5IZu8ZudnP6ds= myname@example.com
Adjust file rights, the authorized_keys2 file must be write/readable only by that user
chmod 600 authorized_keys2
cd ..
chmod 700 .ssh
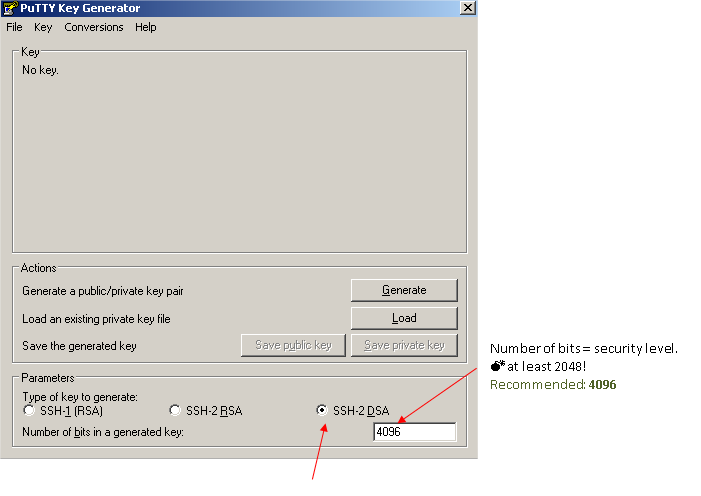
How-to generate private / public keys in Windows
You can generate private / public keys with PuttyGen = Putty key generator.
When the keys are OK, you have to enter a key pass-phrase. Your pass-phrase must be:
- long (> 15 characters)
- hard to guess
- with letters + signs + numbers
Reminder
how to choose your passphrase and protect it: http://www.alcf.anl.gov/resource-guides/user-authentication-policies
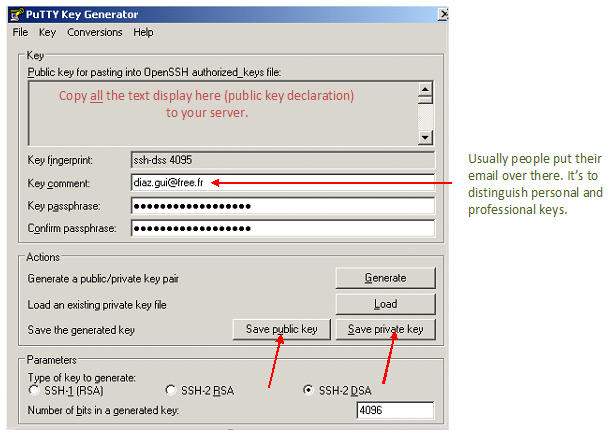
Then, save your keys!
You should be the only one to access the save location.
Configuration changes
vim /etc/ssh/sshd_config
Allow empty password
PermitEmptyPassword yes # allow empty password in favor of RSA keys
Restart SSH server
/etc/init.d/ssh restart
Create profile
Auto-login
Attach private key
Save profile
Go back to the main screen Session and save your changes.
Click on “open” to initialize connection.
Login procedure
Type your passphrase on system request
Access is granted!
Disable standard username / password login
Edit the configuration file
- vim /etc/ssh/sshd_config
Adjust the line:
to:
Fail2ban
see Fail2ban#SSH_configuration
SSH client
Linux
# syntax
ssh user@server -p portNumber
# example
ssh root@daxiongmao.eu -p 4422
References
Source: http://www.howtoforge.com/ssh_key_based_logins_putty
Windows - putty software: http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html