Difference between revisions of "SSH server local key"
(Created page with "Category:Linux =SSH server configuration - Authentication with RSA keys= ==Introduction== If you’d like to increase the authentication process you can use authentic...") |
|||
| Line 111: | Line 111: | ||
/etc/init.d/ssh restart | /etc/init.d/ssh restart | ||
</syntaxhighlight> | </syntaxhighlight> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| Line 145: | Line 116: | ||
=References= | =References= | ||
| − | |||
Source: | Source: | ||
* Public / private key theory: http://en.wikipedia.org/wiki/Public_Key_Cryptography | * Public / private key theory: http://en.wikipedia.org/wiki/Public_Key_Cryptography | ||
* http://www.howtoforge.com/ssh_key_based_logins_putty | * http://www.howtoforge.com/ssh_key_based_logins_putty | ||
Revision as of 14:27, 8 August 2014
Contents
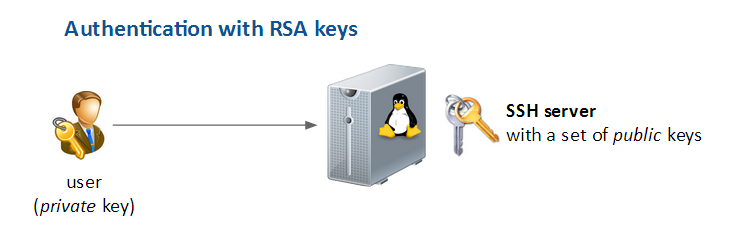
SSH server configuration - Authentication with RSA keys
Introduction
If you’d like to increase the authentication process you can use authentication by private/public key.
- Generate new private / public keys on your own computer
- Put the public key on the remote SSH server
- Only the person with the private key can be authenticate on the server
For instance, this is how hosting company such as OVH can log on your system.
Security improvement: remove password authentication
When the key authentication is working you can remove the default access by login / password. Then, only people with a valid private/public key pair can log in.
That way, there is no way for brute-force attacks to be successful, so your system is more secure.
Declare the public key on the server
You have to:
- log in to your SSH server with the user that’s gonna use this key
- Go to user's home directory
- Create a .ssh folder (if there was none before).
cd ~
mkdir .ssh
cd .ssh
Add the new public key to the list of allowed keys:
vim authorized_key
Prefix your key with:
- RSA: ssh-rsa
- DSA: ssh-dss
Then paste the public key in one line - the public key mustn't be change or separated in 2 lines!
# Example:
ssh-rsa AAAAB3NzaC1yc2EA[...]Lg5whU0zMuYE5IZu8ZudnP6ds= myname@example.com
ssh-dss AAAAB3NzaC1yc2EA[...]Lg5whU0zMuYE5IZu8ZudnP6ds= myname@example.com
Adjust file rights, the authorized_keys file must be write/readable only by that user
chmod 640 authorized_keys
cd ..
chmod 700 .ssh
Configuration changes
vim /etc/ssh/sshd_config
Allow empty password
PermitEmptyPassword yes # allow empty password in favor of RSA keys
Do not allow password authentication
Once you've checked that the key authentication is working you can disable the standard authentication with password. :) With that option enabled all brute-force attacks will failed.
!!BE CAREFUL !!
Once that setting is enable there is no rolling back from it. You might get kicked for good from your own server.
PermitEmptyPassword yes # That must be set to YES
PasswordAuthentication no # Do not allow standard login + password anymore. Only key authentication is allowed.
Restart SSH server
/etc/init.d/ssh restart
References
Source:
- Public / private key theory: http://en.wikipedia.org/wiki/Public_Key_Cryptography
- http://www.howtoforge.com/ssh_key_based_logins_putty